Human & Machine Identity
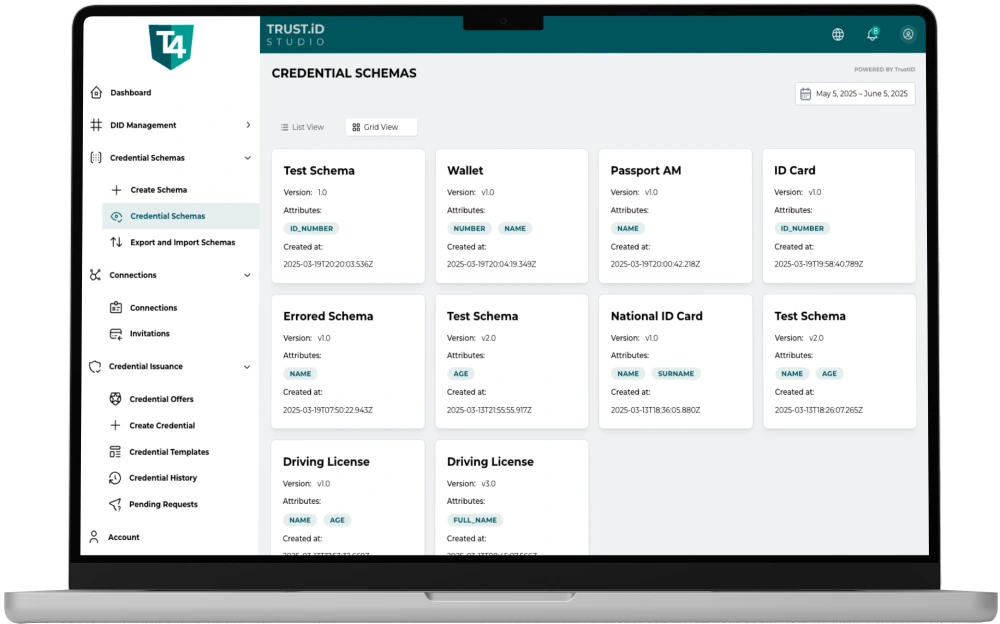
Table Of Content
Overview
In our increasingly digitized world, the need to secure and manage both human and machine identities has become a fundamental requirement.
The traditional identity systems designed for humans alone no longer suffice in a landscape where devices, applications, and automated systems play a critical role. TrustiD addresses this gap by delivering a robust, standards-based platform that integrates human and machine identities seamlessly, ensuring secure interactions, operational agility, and regulatory compliance across industries.

This fragmentation creates silos, increasing the risk of misconfigurations and hindering consistent access control across the ecosystem. Increased Attack Surface Machines and devices — from IoT sensors to autonomous vehicles and APIs — represent a growing attack vector. Without strong identity verification, these endpoints can be hijacked, misused, or exploited to launch attacks within or outside the network.
Limited Interoperability Different standards and protocols make it hard for human and machine identities to be consistently recognized across systems. Legacy systems and vendor-specific identity management solutions can further complicate this integration. Scalability Bottlenecks As the number of devices and users grows exponentially, manual processes for managing identities (like onboarding, credential revocation, or updates) quickly become impractical. Enterprises need a platform that can scale dynamically with their growth.
Regulatory Compliance Regulatory frameworks increasingly require precise control and reporting over how human and machine identities are managed, from who has access to what data to detailed audit logs. Non-compliance risks legal consequences and reputational damage.
TrustiD’s Solution for Human & Machine Identity TrustiD was designed to tackle these challenges head-on by providing:
Privacy-First Approach With TrustiD
Sensitive user data stays under the control of the owner (human or machine), and selective disclosure ensures that only the minimum required data is shared for each interaction.
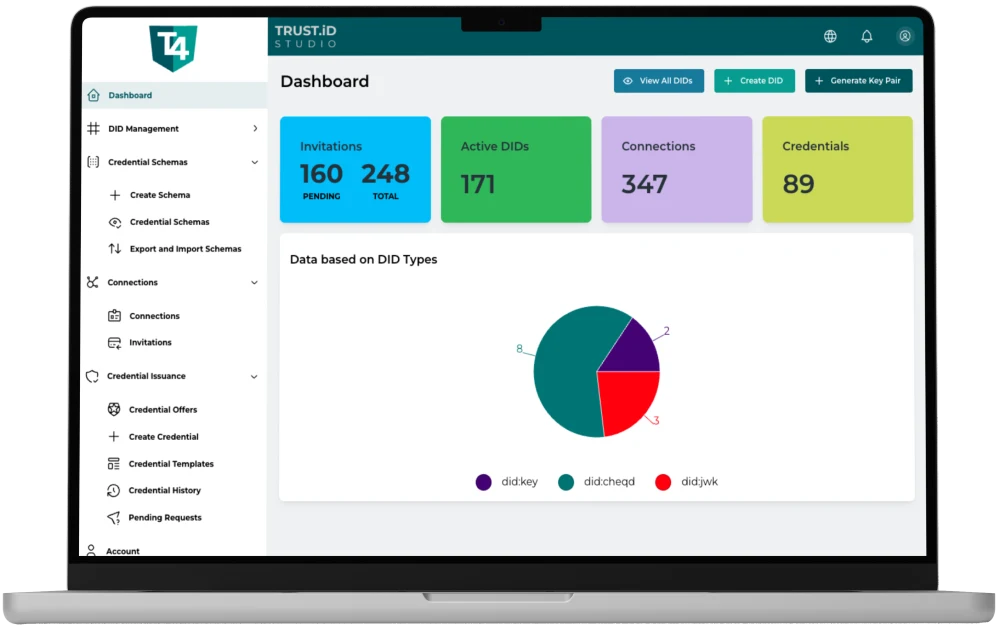
How it Works
- Issuance of Human & Machine Credentials Whether you’re onboarding a new employee, an API client, or a connected IoT device, TrustiD assigns each a DID and generates verifiable credentials that attest to their identity and attributes.
- Decentralized Verification When accessing a resource (like a protected API endpoint or sensitive dataset), the human or machine presents its verifiable credential. TrustiD enables relying parties to cryptographically verify this credential using open standards and optionally distributed ledgers.
- Dynamic Access Control TrustiD’s policy engine uses these verified credentials to grant or deny access in real-time, ensuring that only authorized identities can interact with sensitive resources.
- Audit Trails & Compliance All interactions are logged immutably. Enterprises can provide regulators with detailed records of who accessed what and when, without exposing personal data beyond what is strictly needed.
Real-World Applications of TrustiD’s Human & Machine Identity Solution
- IoT Device Management For an energy company deploying thousands of smart meters across a city, TrustiD ensures each device has a unique identity and verifiable credential. Unauthorized devices can’t spoof or inject data into the system.
- API-Driven Ecosystems Financial services
firms can authenticate external applications and APIs with cryptographically verified machine credentials, preventing API abuse and data leaks. - Workforce & Contractor Access
Large organizations with dynamic workforces use TrustiD to issue and manage employee and contractor credentials, enabling secure access to digital systems while ensuring principle of least privilege. - Hybrid Human-Machine Workflows In manufacturing, where humans operate alongside automated robots, TrustiD ensures that only authorized machines work on production lines, and only authorized humans can control or override them.
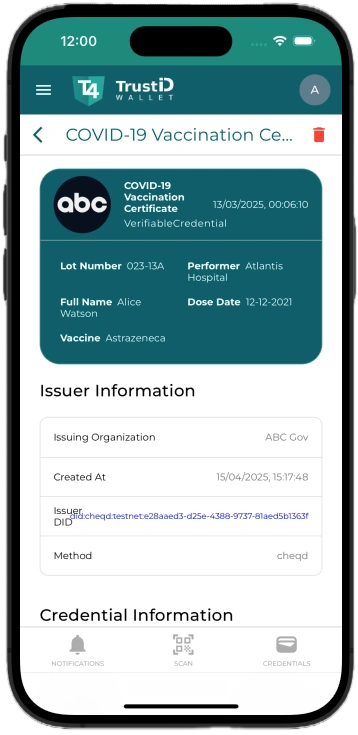
Key Benefits
- Stronger Security Eliminate weak links caused by fragmented identity systems. TrustiD’s verifiable credentials prevent identity spoofing and reduce risks of insider threats and external attacks.
- Operational Efficiency By automating identity lifecycle tasks (like revoking a credential when a device is decommissioned or an employee leaves), TrustiD slashes administrative burden and reduces human error.
- Interoperability & Future-Proofing
TrustiD supports open standards like OpenID4VC, DIDComm, and Verifiable Credentials, making it future-ready as digital identity standards evolve. - Cost Reduction With automation and self-service capabilities, organizations reduce the costs associated with traditional identity management systems. There’s no longer a need for multiple identity platforms to handle humans and machines separately.
- Transparent Compliance Detailed, cryptographically signed logs make it easy to demonstrate compliance with GDPR, ISO 27001, SOC2, and other regulatory frameworks.
Conclusion
As enterprises evolve into digital-first ecosystems, the lines between human and machine interactions blur. TrustiD stands at the forefront of this evolution — unifying human and machine identities under one secure, scalable, and privacy-preserving platform. Organizations that adopt TrustiD today not only bolster security and compliance but also position themselves to thrive in an increasingly decentralized and interconnected world.
TrustiD: Unlock the power of human and machine identity in the digital era.














